Continuous compliance at scale
CMMC Compliance
Proactive CMMC compliance assessments and risk-prioritized remediation with Certified-Assessor-ready reports
Supply Chain Security: Evidence-based Cybersecurity Maturity Model Certification (CMMC) Compliance
All DoD prime contractors and sub-contractors handling FCI and CUI must identify, assess and mitigate supply chain-related security threats in their networks through obtaining CMMC 2.0 certification. Aligning to federal government security efforts demonstrates that they can protect their government customers, as well as themselves, from threat-actors.
Nipper solutions are trusted by US military and civilian federal agencies and their prime and sub-contractors to accurately automate network device assessments against trusted security benchmarks and risk management frameworks, including CMMC.
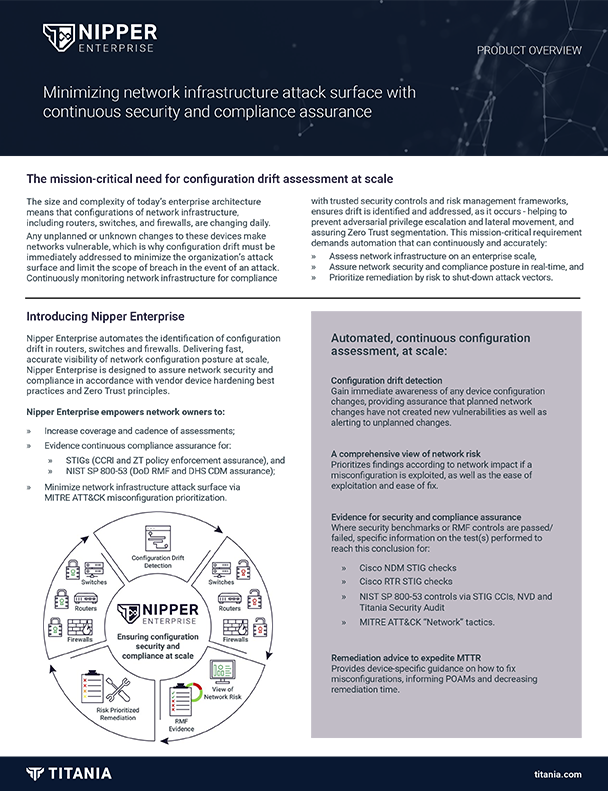
Assess for configuration drift
Gain immediate awareness of any device configuration changes, providing assurance that planned network changes have not created new vulnerabilities as well as alerting to unplanned changes.
Validate compliance with evidence
Accurately automate the assessment of CMMC network security practices relating to network devices, providing pass/fail evidence of compliance in assessor-ready reports.
Improve compliance posture
Prioritize risk by network criticality and receive device-specific guidance on how to fix misconfigurations, informing POAMs and decreasing remediation time.
Continuously validate devices
Determine the security and compliance state of every network device, every day, with ‘pass/fail’ evidence of compliance with vendor hardening guides and security controls.

Research Report
This study reveals that an average of 51 network device misconfigurations were discovered in a two-year period with 4% deemed to be critical vulnerabilities that could take down the network within the U.S. Federal Government.

Take a Proactive Approach to CMMC
Establish a baseline to use when creating a roadmap to compliance. Once CMMC 2.0 is codified, organizations in the DoD supply chain will begin being contractually required to adhere to the updated framework.
Assure Continuous Compliance
Detect non-compliances and effectively manage configuration drift with CMMC assessments of every router, switch and firewall, on an up-to-hourly basis.


Automate Assessor-ready Reporting
Simplify compliance reporting processes for CMMC network infrastructure requirements with Certified-Assessor-ready reports within minutes.
Prioritize Remediation of Exploitable Risks
Determine which software vulnerabilities and misconfigurations to fix first using automated prioritization of findings with mitigating advice to inform remediation workflows. Quickly and accurately check devices are configured according to vendor hardening guides and comply with organizational/ regulatory security policies.


Deliver Security from CMMC Compliance
Automate an accurate, timely, and scalable approach to CMMC compliance, ensuring proactive security as key to protecting agency and supply chain networks from preventable attacks.
Continuous Security & Compliance, at Scale
Nipper Enterprise delivers fast, accurate visibility of network configuration posture at scale to ensure ongoing compliance in accordance with CMMC requirements.
Explore Related Resources
Looking for continuous configuration assessment to:
-
Evidence compliance with CMMC and NIST SP 800-171?
-
Minimize your attack surface?
-
Validate the security of every router, switch and firewall, everyday?